Early in July, I got some bug report emails about Booko’s login via Yahoo! no longer working. A quick investigation confirmed it.
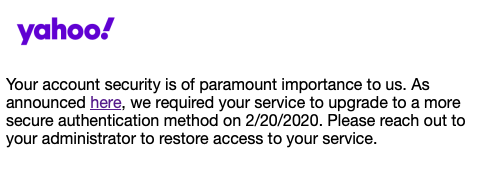
Unfortunately, I missed that announcement and so migrating to Yahoo’s OIDC (OpenID Connect) was at the top of my todo list.
OIDC is an identity service which runs on top of OAuth 2.0. Yahoo’s migration document provides clear instructions on how to do this.
First up, let’s use the OAuth2 Ruby gem and get an OAuth client to use. In real code, you might pass in a ‘service’ argument, for say, Google or any other OIDC provider.
def yahoo_client
client_id = Rails.application.credentials.yahoo_client_id
client_secret = Rails.application.credentials.yahoo_client_secret
site = 'https://api.login.yahoo.com'
token_url = '/oauth2/get_token'
authorize_url = '/oauth2/request_auth'
state = session[:state] ||= SecureRandom.hex
OAuth2::Client.new(
client_id, client_secret,
site: site,
authorize_url: authorize_url,
token_url: token_url,
state: state)
endIn your controller, you’ll need an action to perform an OAuth login. As part of the redirect, you need to provide a URL that the user will be redirected back to.
def oauth_login
client = get_yahoo_client
scope = 'openid'
response_type = 'code'
yahoo_url = client.auth_code.authorize_url(
redirect_uri: 'https://booko.info/process_oauth',
scope: scope,
nonce: session[:state])
redirect_to yahoo_url, status: 303
When a user hits the “Login via Yahoo!” button on your site, they’ll need to hit this action. The action builds an OAuth client and then redirects the user over to Yahoo! to sign in and will ask if they want to authenticate to your site and maybe hand over their email address. Yahoo! will then send the user back to the redirect_url you passed into the OAuth client.